34+ intrusion detection system diagram
It can however log messages generated by Windows. SolarWinds Security Event Manager SEM is an intrusion detection system designed for use on Windows Server.

Fiber Optic Cable An Overview Sciencedirect Topics
The IDS sends alerts to IT and security.
. Intrusion Detection System for the Internet of Things Based on Blockchain and Multi-Agent. Use Createlys easy online diagram editor to edit this diagram collaborate with others and export results to. 191798951 stock photos online.
Intrusion Detection Systems were available before Intrusion Prevention Systems. To implement Intrusion Detection System with the help of Face recognition in terms of motion. An intrusion detection system IDS.
Intrusion detection system classic by Nikhil Aggarwal. Download scientific diagram Intrusion detection system discussed 34. New users enjoy 60 OFF.
The basics of a IDS is if there is an attack on the network the IDS is going to be sitting there and analyzing. Download 99 Diagram Intrusion Detection System Stock Illustrations Vectors Clipart for FREE or amazingly low rates. INTRODUCTION 11 Purpose The aim of the project is to.
Also intrusion prevention system or IPS is a device or software application that monitors a network or systems for malicious activity or policy. An intrusion detection system IDS is an application that monitors network traffic and searches for known threats and suspicious or malicious activity.
2
2
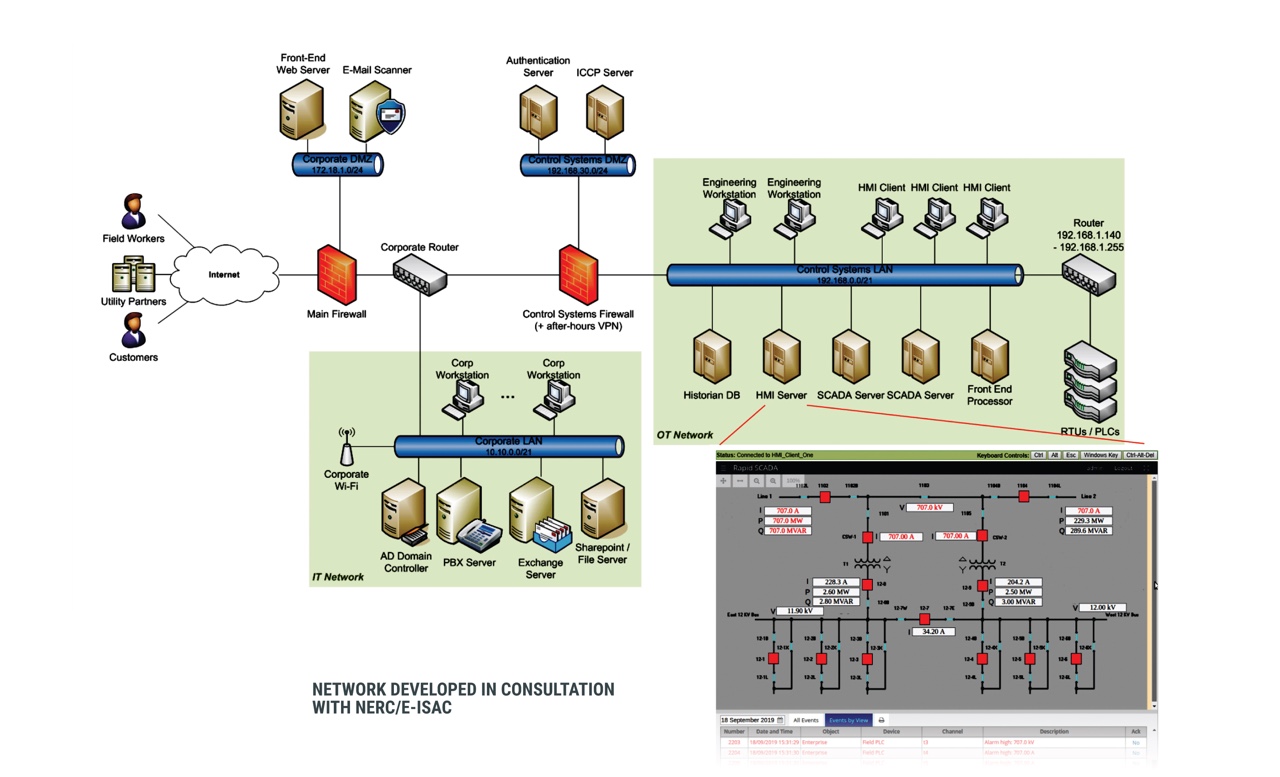
Cyrin Resources
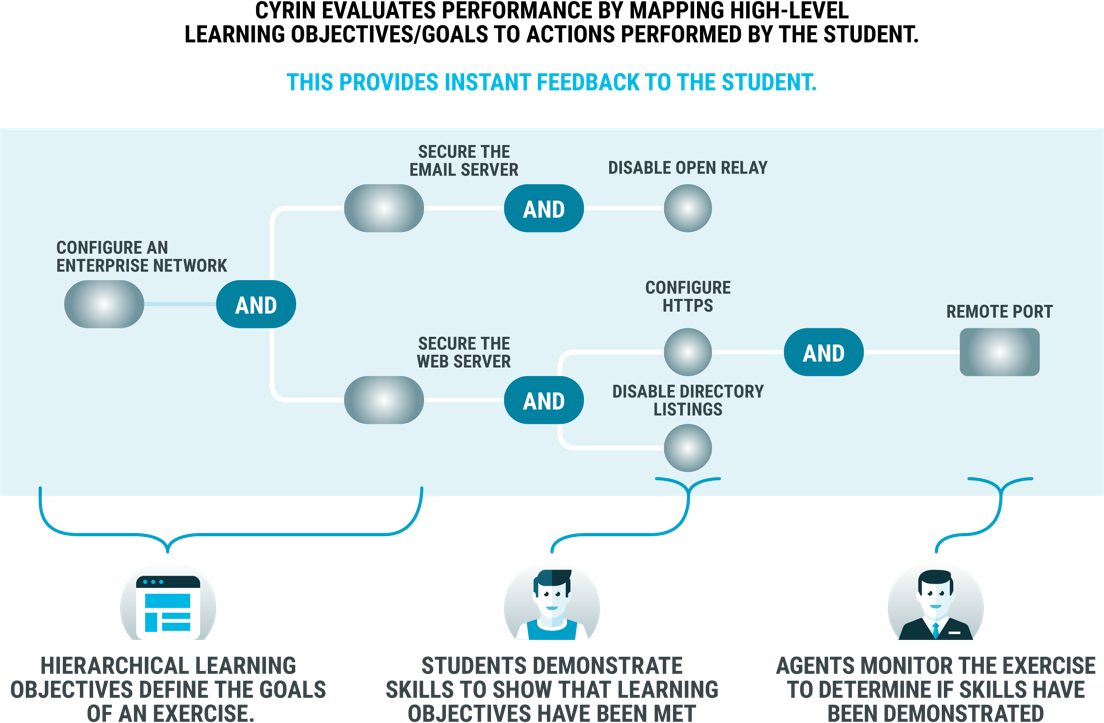
Cyrin Resources
2
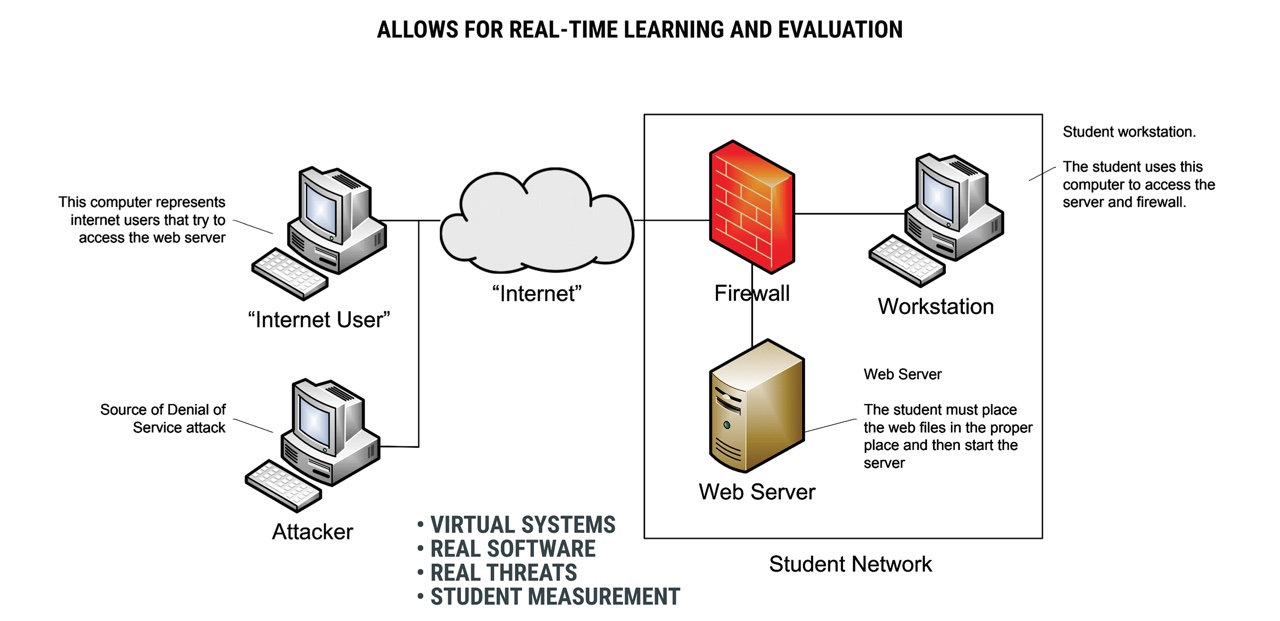
Cyrin Resources

Fiber Optic Cable An Overview Sciencedirect Topics

Fiber Optic Cable An Overview Sciencedirect Topics

Fiber Optic Cable An Overview Sciencedirect Topics
A Survey Of Artificial Intelligence Techniques For Cybersecurity Improvement Document Gale Academic Onefile
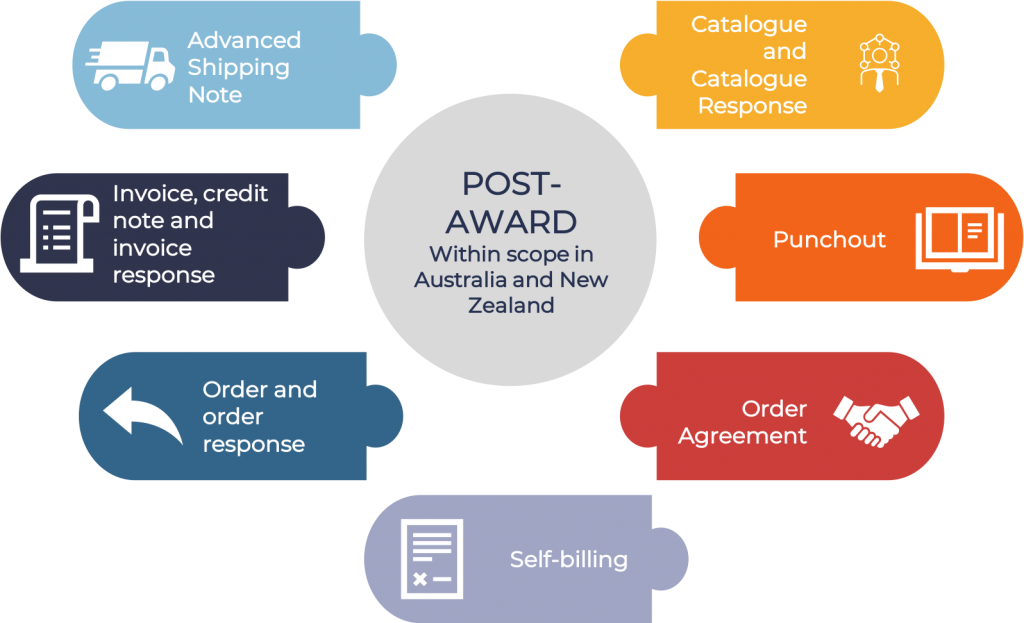
What Is Peppol A Simplified Guide To All Things Peppol
A Survey Of Artificial Intelligence Techniques For Cybersecurity Improvement Document Gale Academic Onefile
2

Fiber Optic Cable An Overview Sciencedirect Topics

K10vh0zaib9zbm
2
A Survey Of Artificial Intelligence Techniques For Cybersecurity Improvement Document Gale Academic Onefile